Backstory: Yesterday, I had a post on Reddit that linked to the https:// url here. While relaxing for the night and sipping on a cold frosty one, I decided to check out how the post was doing. I did this on my Samsung SMT-320 Android Tablet, which is stuck on a nice old and crusty Android 4.4.2. And to my surprise, the site, gave me a giant security error.

What the shit? This is unacceptable! I paid a good $.99 for that cert! Why is it broken! I could of popped some tags with that money, ya' bastards!
So, I got up, got another frosty one, and grabbed my laptop. It was obviously time to shame someone on Twitter. But first, lets fire up my favorite SSL cert checker and find out what is wrong. (And by 'favorite' I mean, first result on google.)
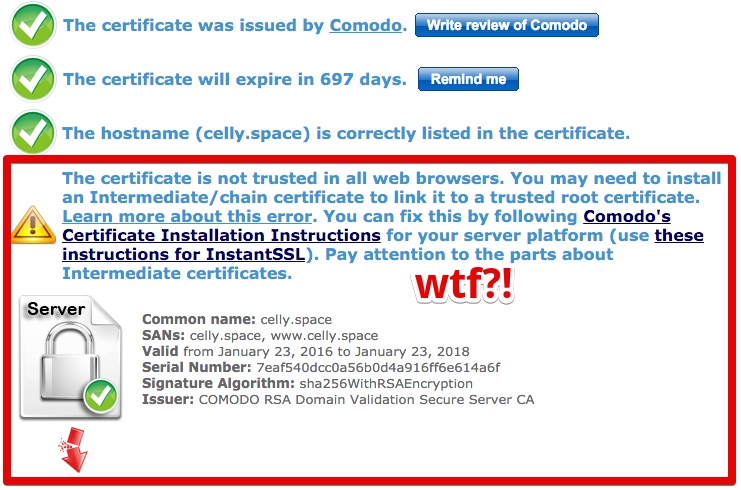
Whoa. Wait. This is my fault? Damnit, not again. Time to lay off the frosty ones, because this makes for yet another awkward Twitter shame.
The Cause?
In my post about setting up Ghost CMS on an AWS t2.nano, I talked about how you can get an inexpensive SSL cert from Namecheap.com and there were a bunch of walk thrus to help you install it. Well, one thing none of these walk thrus talk about is intermediate certs, and why you need them.
And, to be honest, up until last night, short of single email with an ops guy (Which just so happened to be 2 weeks ago, holy Baader-Meinhof batman), I had never heard of a need for intermediate certs in this type application and the exact reason for them. Luckily, Wikipedia had:
There are two types of certificate authorities (CAs), root CAs and intermediate CAs. In order for a certificate to be trusted, and often for a secure connection to be established at all, that certificate must have been issued by a CA that is included in the trusted store of the device that is connecting.
If the certificate was not issued by a trusted CA, the connecting device (e.g., a web browser) will then check to see if the certificate of the issuing CA was issued by a trusted CA, and so on until either a trusted CA is found (at which point a trusted, secure connection will be established) or no trusted CA can be found (at which point the device will usually display an error).
tl;dr / ELI5: Intermediate certs validate the color yellow of the yellow brick road your data is following on its way to the Emerald SSL city which protects it from the prying eyes of the winged monkeys.
And, what happened in my case -- The Wicked Witch (Being played by Samsung) is holding back the software on my tablet so I don't have the fresh new safe shades of yellow installed. So it couldn't validate if the yellow brick road I was following was a secure meadow dandelion yellow -- or an evil shade of yellow snow...
/me Shakes fist at Samsung
Samsung slaps Celly around with a large trout... Again.
The solution
Luckily this can be easily solved by adding in intermediate certificates to my existing certificate. Which, honestly, should be done regardless but no one ever really mentions these.
First, find the intermediate/root certificates needed. In my case I was lucky, and my provider Namecheap.com already provides the bundles for you. The trick here is to find the right bundle based off of your product, which in my case was the RapidSSL SHA-2 bundle.
Once you download and copy the certificates to you server, you need to append them onto your current certificate. My steps on AWS Linux running NGINX were:
$ sudo cp /etc/ssl/celly.space.crt /etc/ssl/celly.space.crt-in_case_i_f_up
$ sudo cat COMODO_DV_SHA-256_bundle.crt >> /etc/ssl/celly.space.crt
$ sudo /etc/init.d/nginx reload
Reloading nginx: [ OK ]
(Of course, your files / directories will be different)
Now, Time to test my SSL setup again...
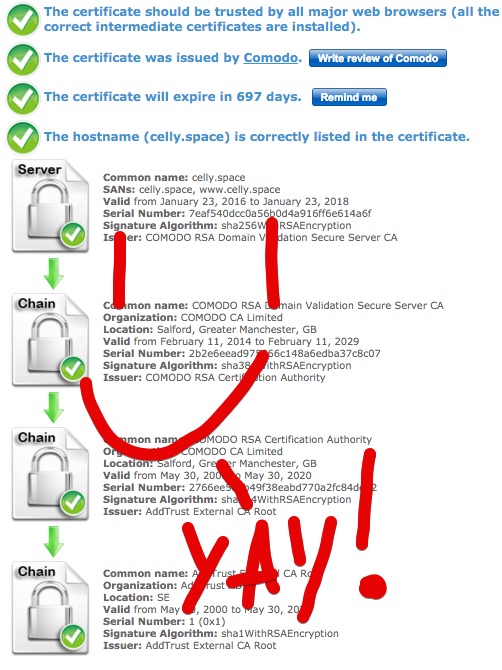
w00t! It's all good. Range rover all wood.
... Time to grab another cold frosty one and celebrate ...